Cyber Security
Strengthen your
Cyber Defenses
Botek and Splunk for Security provides industry-leading detection, investigation and response capabilities.
USE CASES
A comprehensive solution built for
Security Monitoring
Never miss a threat.

Cloud Security
Regain visibility into your environment.
Threat Hunting
Find weaknesses before bad actors do.

Auditing and Compliance
Measure and report on your security posture.

Advanced Threat Detection
Detect known and unknown threats.
SOC Management and Collaboration
Coordinate your tools and team for peak performance.
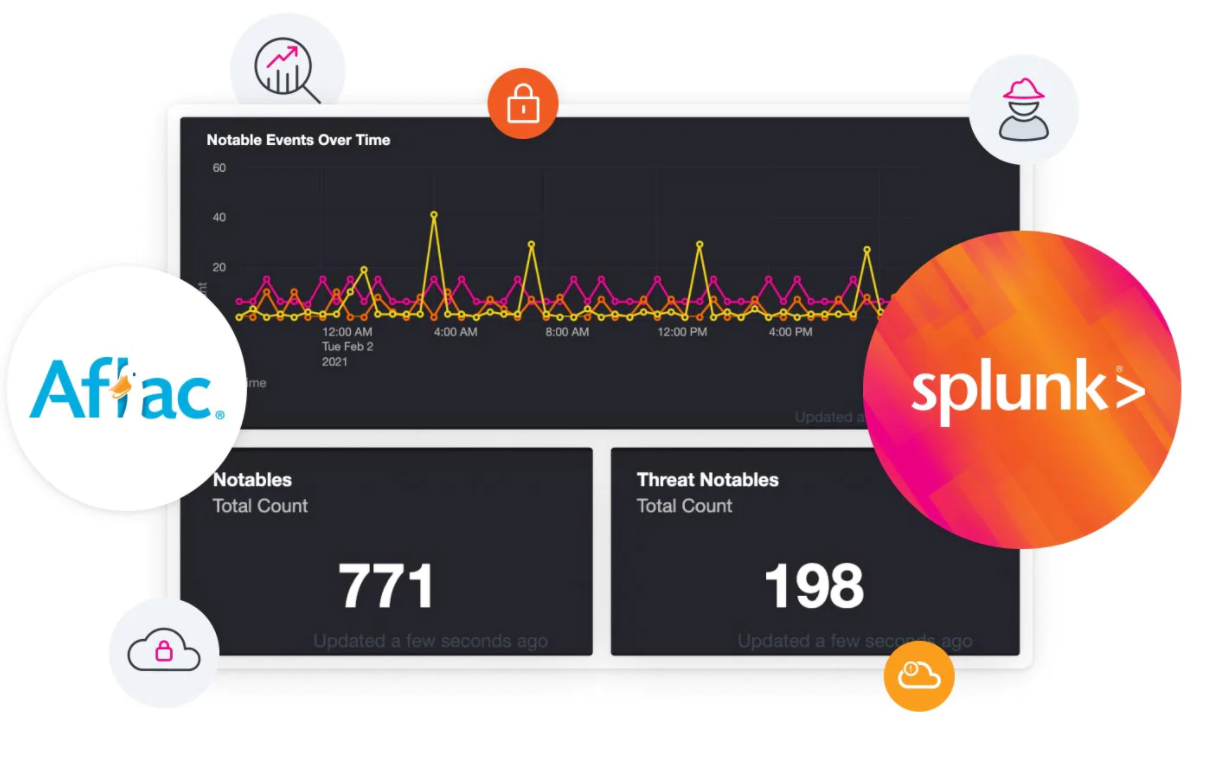
SECURITY MONITORING
Protect your business and people proactively with cloud security.
Out of the box and custom correlation searches help find threats, determine security posture and compliance through continuous security monitoring of critical entities.
ADVANCED THREAT DETECTION
Aggregate, prioritize and manage wide varieties of threat.
OUR SOLUTION
Add security to your existing systems.
Security Features
Get what you need to detect and respond fast.

Monitor at the speed of Business
Use conitnous monitoring, ad hoc search, static and dynamic searches, and visual correlations to determine malicious activity.

Prioritize and Act on Risk
Implement risk-based alerting to focus your team's attention on threats not false postives.
Agnostic End-to-End Visibilty
Gain valuable security-specific insight across cloud, on-premises and hybrid services.

Access Security Posture
Identifies potential incidents, compromised systems or both by monitoring for vulnerabilities that lead to breaches.

Accurate Monitoring
Maintain a consistent and accurate monitoring process using continuous monitoring capabilities that enable predefined correlation rules and the ability for security practitioners to easily customize rules.

Compliance
We help organizations establish a historical baseline for audits and understanding the scope and data in your infrastructure while helping with compliance requirements.

Flexible, Customization Security
Simply use out-of-box or customized correlations, searches and visualizations of all monitored data in real time to get a clear perspective of your organization's security posture.

Scalable Analytics-Driven Monitoring
We enable security analysts to accurately identify root cause and make informed decisions on issue remediation.
